Cybersecurity Assessment and Pen Testing Services Hong Kong
Secure Your Systems Meet Regulatory Standards.
Streamline your licensing journey by aligning your security framework with the SFC’s stringent cybersecurity standards. Our specialized Cybersecurity Assessment and Pen Testing services for Virtual Asset Trading Platforms (VATPs) and other licensing aspirants ensure compliance every step of the way.
- Annual Pen Testing Service for Compliance Reporting
- Annual Vulnerability Scanning Services
- Cybersecurity Assessment Service Hong Kong & Reporting
Request Consultation
Our Services
Cybercrime and Cyber-Attacks are becoming more prevalent with each passing day. Over half of small and medium businesses (SMB) have reported being the victims of cybercrimes. Every day, there are new headlines about data breaches, hackings, Cyber-Attacks, and various forms of crimes against businesses.
Professional Cybersecurity Assessment and Pen Testing Services Hong Kong and Singapore. Our Pen Testing Services Hong Kong & Singapore are designed to achieve maximum compliance and security for our customers.

Service Scope
- Scoping and Planning
- Data Gathering & Analysis
- Pen Testing & Vulnerability Scan
- Reporting and Recommendations
- Presentation and Consultation
Cybersecurity Assessment Service
Overview
Our Cybersecurity Posture Assessment service provides a holistic evaluation of an organization's security controls, policies, and procedures. We employ a multi-faceted approach that combines automated scanning, manual testing, and expert analysis to deliver a comprehensive and actionable assessment.
Key Benefits
- Identify Vulnerabilities: Continuous surveillance of the network traffic to identify suspicious activities.
- Reduce Risk: Utilization of advanced machine learning techniques to detect anomalies and potential threats.
- Improve Compliance: Immediate containment and remediation of identified threats to prevent further damage.
-
Enhance Security Awareness: Detailed reports and analytics to provide insights into the nature and origin of threats.
- Optimize Security Investments: Prioritize security investments based on identified risks and vulnerabilities.
- Gain a Clear Understanding: Obtain a comprehensive view of your organization's security posture.
Methodology
Our Cybersecurity Posture Assessment methodology is based on industry best practices and standards, including:
NIST Cybersecurity Framework
ISO 27001
CIS Controls
OWASP
We tailor our methodology to meet the specific needs of each organization.

Annual Pen Testing Benefits
- Comprehensive Threat Detection - Penetration testing helps to identify vulnerabilities in an organization’s IT infrastructure, applications, and network
- Risk Management - By pinpointing and addressing vulnerabilities, penetration testing aids in risk management.
- Regulatory Compliance - Regular penetration testing helps organizations meet regulatory standards and avoid potential fines or legal repercussions.
- Safeguarding Reputation - A security breach can have devastating effects on an organization's reputation and customer trust.
- Cost-Effective Security - Investing in penetration testing can save costs in the long run by preventing costly data breaches and downtime.
Penetration Testing Service
Overview
A penetration test, also known as a pen test, is a way to simulate cyber-attack against an IT infrastructure to identify exploitable vulnerabilities. The test is conducted against internet or internal servers, web apps, network devices and anything related to IOT. Our network pent test service in Hong Kong provide the hybrid approach which relies upon both the manual and automated methods of testing.
Test Type Coverage
- WHITE BOX - As the name defines, this type of test is basically conducted based on all information available about a system or application. The customer provides proper logins for testing specially created for this type of testing to produce the best results for a test.
- GREY BOX - This type of test mixes the testing methodologies from Black Box Pen test and White Box Pen Testing. Customer shares partial information to conduct such testing.
- BLACK BOX - In a Black Box Pen test, the client does not provide with any information about their infrastructure. For internal tests the customer may provide no more than a network point for the tester to connect to. For external tests, this may simply be a URL or even just the company name that is in scope for assessment.
Our Pen Testing Services Scope
- Web Application Pen Testing - Our web application penetration testing services focus on identifying vulnerabilities in your web applications. We assess everything from authentication and authorization mechanisms to session management and data validation processes.
- Network Pen Testing - Network penetration testing services are designed to evaluate the security of your network infrastructure. We identify and exploit vulnerabilities in your firewalls, routers, switches, and other critical components to ensure robust network security.
- Cloud Security Pen Testing- As businesses move to the cloud, ensuring the security of cloud-based assets is paramount. We offer cloud security testing services to evaluate the security of your cloud infrastructure and applications.
- Social Engineering Assessments- Human factors are often the weakest link in security. Our social engineering assessments test your organization’s susceptibility to phishing, baiting, and other social engineering attacks.

Our Process
- Initial Assessment - We begin with a comprehensive assessment of your current security posture. This includes understanding your IT environment, identifying critical assets, and evaluating existing security measures.
- Automated Scanning - Using advanced scanning tools and technologies, we perform automated scans of your network, systems, and applications.
- Detailed Analysis - Once the scanning is complete, our experts analyze the findings to determine the severity and impact of each vulnerability.
- Remediation Planning - We work closely with your team to develop a remediation plan that addresses each vulnerability.
- Follow-Up Scanning - After remediation, we conduct follow-up scans to ensure that all vulnerabilities have been addressed and to verify the effectiveness of the implemented security measures.
Vulnerability Scanning Service
Overview
Vulnerability assessment is the procedure to define, identify, classify and prioritise vulnerabilities in systems, applications, or overall scoped infrastructure.
This also provides an organization with the information about the current state of their entire infrastructure in terms of security exposure.
Organization of any size should have a plan and program for vulnerability assessments and Dual Layer Cyber Tech provides comprehensive managed and one off assessment services to its clients.
In our unique approach we address the following types of assessments during an engagement and work closely with client’s team to provide them with full feedback to fix such vulnerabilities.
Key Features
- Network Based Scans and manual checks This kind of testing identifies network connected devices and see if there are possible issues with configurations or known or unknown vulnerabilities.
- Host based scans – These are mainly run against the host systems which could be servers hosting different services would be scanned against the threats.
- EndPoint based scans – Such scans are run against each individual endpoint on the network and identify the state of each system and to provide the accurate picture of the endpoints in a given environment
- Wireless Network scan – This identifies the related exposure and weaknesses in an organizations WiFi Network and its configurations. Application and Database Scans are run against the custom or third party applications, web apps or databases and identify the standard of the configuration and vulnerabilities.
How We Help You Meet Cybersecurity Standards
- Penetration Testing
- Vulnerability Assessment
- Security Controls
- Incident Response
- DR & BCP
- IT Audit
- Compliance Monitoring
Penetration testing involves a systematic approach to identifying and addressing vulnerabilities in systems and networks. Below is a summarized process:
Pre-Engagement: Define objectives, scope, legal agreements, and timelines.
Reconnaissance: Gather information through passive and active methods, including network scanning and potential social engineering.
Vulnerability Identification: Use automated tools and manual checks to discover weaknesses.
Exploitation: Simulate attacks to exploit vulnerabilities and assess impact.
Post-Exploitation: Analyze accessed data, test persistence, and clean up systems.
Reporting: Document findings, provide risk analysis, and offer remediation recommendations.
Remediation & Re-Testing: Support fixes, verify mitigations, and update reports.
Continuous Improvement: Learn from outcomes, enhance awareness, and schedule regular tests.
This concise approach ensures actionable insights to strengthen cybersecurity.
Vulnerability assessment focuses on identifying and evaluating vulnerabilities within an organization’s systems and networks to enhance security posture. Below is a summarized process:
Preparation: Define the scope, objectives, and target systems. Establish necessary legal agreements.
Scanning: Use automated tools to identify known vulnerabilities in systems, applications, and networks.
Analysis: Assess scan results to determine the severity, potential impact, and likelihood of exploitation.
Prioritization: Rank vulnerabilities based on risk levels and business context to focus on critical issues.
Reporting: Provide a comprehensive report detailing findings, their impact, and prioritized recommendations for remediation.
Remediation Support: Offer guidance to address identified vulnerabilities effectively.
Re-Assessment: Conduct follow-up scans to verify that vulnerabilities have been mitigated or resolved.
Ongoing Monitoring: Schedule regular assessments to maintain a proactive security approach.
This structured process helps organizations reduce risks and strengthen defenses against cyber threats.
IT compliance reviews and advisory services help organizations ensure their security controls meet regulatory and industry standards. Below is a summarized process:
Preparation and Scope Definition: Define compliance objectives, scope of review, and applicable standards (e.g., ISO 27001, NIST, COBIT etc.)
Assessment of Existing Controls: Evaluate the effectiveness of current security measures such as:
Multi-Factor Authentication (MFA): Ensure MFA is implemented for critical systems.
Encryption: Verify encryption methods for data at rest and in transit.
Secure Configuration: Assess secure baseline configurations for systems and applications.
Documentation: Review and update policies, procedures, and audit logs.
Gap Analysis: Identify areas where controls fall short of compliance requirements.
Risk Prioritization: Rank gaps based on their potential impact and likelihood of exploitation.
Recommendations: Provide actionable steps to remediate identified gaps, including policy updates, technology changes, and staff training.
Implementation Support: Assist in deploying new controls and updating existing ones to achieve compliance.
Compliance Reporting: Document compliance status, improvements made, and remaining gaps in a formal report for stakeholders and regulators.
Ongoing Advisory: Offer continuous guidance to adapt to evolving standards and maintain compliance.
This process ensures that organizations not only meet regulatory requirements but also establish a robust security posture to mitigate risks.
Incident response planning ensures organizations can effectively detect, respond to, and recover from cybersecurity incidents. Below is a summarized process:
Preparation: Develop an incident response plan (IRP) outlining roles, responsibilities, communication strategies, and escalation procedures. Train staff and establish an incident response team (IRT).
Detection and Identification: Implement monitoring systems to identify and confirm potential incidents. Use tools such as SIEMs, IDS/IPS, and endpoint detection systems.
Containment: Limit the spread of the incident by isolating affected systems, restricting access, and mitigating immediate risks.
Eradication: Identify the root cause of the incident and remove malicious files, compromised accounts, or vulnerabilities.
Recovery: Restore systems to operational status using backups and verify that no further vulnerabilities or threats remain. Monitor systems closely during this phase.
Post-Incident Analysis: Conduct a thorough review to document the incident, analyze the response process, and identify areas for improvement. Prepare a detailed incident report.
Continuous Improvement: Update the incident response plan based on lessons learned and adapt to emerging threats and trends.
This structured approach ensures a swift and effective response to cybersecurity incidents, minimizing damage and downtime while strengthening resilience.
- Stress Testing, Evaluate how systems perform under extreme conditions.
- Conducting drills and exercises that mimic real world DR situations
- Preparing BCP and DR policies, plans and Testing methodologies.
- Provide guidance on improving system uptime and operational resilience.
In today’s digital age, ensuring business continuity requires comprehensive strategies that cover disaster recovery, business continuity planning, resilience testing, and DDoS protection. By implementing these practices, organizations can safeguard their operations, protect their reputation, and maintain trust with their customers and stakeholders even in the face of unforeseen disruptions.
- Independent, unbiased testing by certified cybersecurity professionals.
- Produce detailed reports designed for regulatory submission.
- compliance achievements and any required remediation steps.
- Aim to improve operational efficiency by identifying and addressing inefficiencies in IT processes.
- Covering IT Governance, Data Management, Access Controls, Security and Risk Management
IT audit services are crucial for maintaining a secure IT environment, ensuring compliance, and improving efficiency. Regular IT audits help organizations stay ahead of risks and maintain a robust IT infrastructure.
- Continuous vulnerability management and penetration testing as part of ongoing maintenance.
- Keep your systems aligned with evolving regulatory and industry standards.
- Provide continuous reporting to demonstrate proactive compliance.
- Compliance monitoring for Data Protection, Privacy, IT Asset Management, Configuration Management, Network Security, Patch Management, Access Management and Technical controls
Compliance monitoring is essential for IT, systems infrastructure, and cybersecurity. It ensures adherence to legal, regulatory, and internal requirements, mitigating risks, enhancing trust, and protecting sensitive information. Implementing robust compliance monitoring practices helps organizations navigate complex regulations and maintain a secure and compliant environment.
OUR METHODOLOGY
Penetration Testing & Cybersecurity Audit
Our approach combines penetration testing with IT audit best practices based on NIST, ISO 27001, and international standards. This ensures our clients receive not only technical vulnerability insights, but also business-oriented security assurance that meets compliance and regulatory requirements.
Whether you’re preparing for an ISO 27001 certification audit, aligning with the NIST Cybersecurity Framework (CSF), or meeting other regulatory compliance requirements, our methodology delivers clear, actionable, and audit-ready results.
Scoping & Planning
We define scope, objectives, and compliance needs, ensuring engagement aligns with business priorities, regulations, and security goals while maintaining confidentiality through structured agreements.
Reconnaissance
Our team gathers intelligence, maps attack surfaces, and applies threat modeling to simulate realistic cyberattack scenarios tailored to your industry.
Vulnerability Identification
We combine automated scanning and manual analysis to detect vulnerabilities, misconfigurations, and weaknesses, referencing OWASP, NIST, and MITRE frameworks for comprehensive, coverage.
Exploitation & Impact
We safely exploit vulnerabilities to validate severity, demonstrating real-world business impact such as data leakage, system compromise, and regulatory exposure, without disrupting operational services.
Exploitation & Impact
Our experts assess lateral movement and persistence, validating real risks while measuring detection and response capabilities across networks, applications, and organizational defenses.
Reporting & Re-Testing
We deliver clear executive and technical reports, provide tailored remediation support, and conduct re-testing to confirm vulnerabilities are effectively resolved.
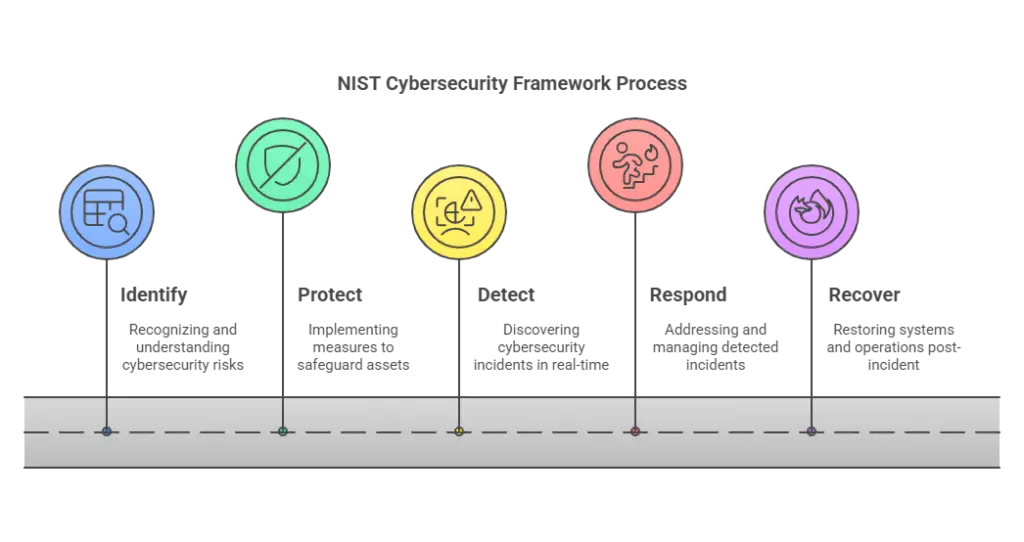
NIST Cybersecurity Framework Adoption
The NIST Cybersecurity Framework enables businesses and enterprises to evaluate the risks they encounter. The framework consists of three parts. The Framework Core presents a range of references, outcomes, and activities associated with aspects and approaches to cyber defense.
The Framework Implementation Tiers help organizations establish their approach to cybersecurity and clarify their stance to all stakeholders. The tier also portrays the degree of sophistication of the management approach. The Framework Profile contains a collection of outcomes the enterprise picked from the categories and subcategories based on its risk evaluation and requirements.
Adopting the NIST Cybersecurity Framework is a strategic decision that can greatly enhance an organization’s ability to manage cyber risks. Our firm’s expertise and comprehensive approach ensure that clients can effectively implement the framework, tailor it to their specific needs, and continuously improve their cybersecurity posture.
By partnering with us, organizations can navigate the complexities of cybersecurity and achieve a robust and resilient system that protects their critical assets and information.
FAQ
What is a Penetration Testing Service and why is it important for my business?
A Penetration Testing Service simulates real-world cyberattacks to identify and exploit vulnerabilities in your systems, networks, or applications. It helps organizations uncover security weaknesses before malicious actors do, reducing the risk of data breaches and compliance violations. We offer compliant Penetration services in Hong Kong with professional reporting services.
How does a Cybersecurity Assessment Service differ from a Penetration Test?
A Cybersecurity Assessment Service provides a comprehensive review of your organization’s security policies, controls, and compliance posture. In contrast, a Penetration Testing Service focuses on actively probing and exploiting vulnerabilities. The assessment is broader and policy-focused, while pen testing is technical and attack-focused.
What is Vulnerability Scanning and how does it benefit my organization?
Vulnerability Scanning is an automated security process that detects known vulnerabilities such as outdated software, missing patches, and misconfigured systems. Regular scans help organizations proactively manage risks and maintain compliance by identifying issues before they’re exploited. Our Vulnerability scanning services in Hong Kong are comprehensive and provides detailed coverage.
Is Vulnerability Scanning enough to secure my systems?
While Vulnerability Scanning Services are crucial for identifying known security flaws, they do not assess the actual exploitability of those flaws. To truly understand risk exposure, it’s recommended to pair scanning with a Penetration Testing Service and a thorough Cybersecurity Assessment Service.
Will Penetration Testing or Vulnerability Scanning disrupt my business operations?
Both Penetration Testing and Vulnerability Scanning Services can be conducted with minimal disruption. We coordinate closely with your IT team to plan tests during off-peak hours and ensure business continuity.
What deliverables should I expect from a Cybersecurity Assessment Service?
A comprehensive Cybersecurity Assessment Service typically includes an executive summary, technical findings, compliance gap analysis, risk ratings, and actionable recommendations to enhance your security posture and meet industry standards like ISO 27001 or NIST.
Are these cybersecurity services necessary for regulatory compliance?
Yes. Services like Vulnerability Scanning, Penetration Testing, and Cybersecurity Assessments are required or strongly recommended by frameworks such as PCI-DSS, HIPAA, ISO 27001, and SOC 2. These services demonstrate due diligence and help organizations meet legal and industry-specific obligations.
What types of Penetration Testing Services are available?
Common types of Penetration Testing Services include:
- External Pen Tests (internet-facing systems),
- Internal Pen Tests (inside the network),
- Web Application Testing,
- Wireless Network Testing,
- Social Engineering Testing, and
- Physical Security Testing.
Our Expertise
Why Partner With Us
-
Proven Expertise
Specialists with globally recognized certifications & years of experience
-
Tailored Solutions
Customized Cybersecurity Services for regulatory compliance
-
Comprehensive Support
Assistance from initial assessments to final Reporting








Take the First Step Towards
Cybersecurity Compliance
Partner with us to ensure your cybersecurity meets IT security and regulatory requirements confidently.
Phone
+852 3700 9988
Address
Unit 1005, 10/F, Prosperity Millennia Plaza,
663 King's Rd, Quarry Bay, HK